Congratulations to the team at Chorus One, who successfully executed the largest attack yet in Tour de SOL!
This week they managed to identify an attack vector allowing them to steal 500 million SOL tokens from the Tour de SOL test network. To understand how they managed to pull off this incredible attack there are a few things you need to know first:
- When we’ve booted up any of our clusters, whether it be for a Dry Run or Stage 1 in Tour de SOL we run several nodes ourselves, before inviting external Validators to jump in
- These nodes that we run, we call bootstrap validators and they start with all of the stakes in the network
- As external Validators join the network, the stake is gradually distributed to them over a period of time which we call epochs, and the duration of each epoch can be up to several days long
- As a result of this large amount of stake typically stays with the bootstrap validator for some time
With the above in mind, the team at Chorus One identified that when it’s a Validators turn to be a leader in the network, and broadcast their transactions to the rest of the network, they can invent any valid transaction they want. Which in itself is not a major issue, so long as the other Validators in the network are honest and will verify the signatures, identify that there is an issue, and then reject the block.
However, Chorus One cheekily sent transactions created a block with bogus signatures and broadcast them to the rest of the network, because they figured out that the code designed to verify transaction signatures was not implemented. other Validators were not verifying the transaction signatures as they should have been. Using this strategy they convinced the network that the 10 SOL tokens were transferred from the Bootstrap Validator to their Validator node instead.
Below is a dump of the first block that Chorus One injected bogus transactions into before they went on to steal the total 500 million SOL:
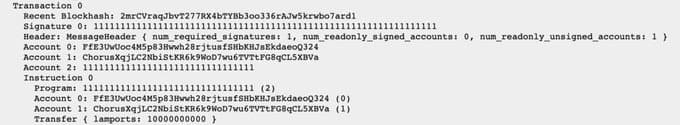
Bogus Transaction
Where Account 0 is our Solana Bootstrap Validator, and Account 1 is Chorus One’s Validator. Notice also the transaction signature of almost all 1’s (format is in Base58) which almost never happens and is highly irregular. And of course, the last line, which highlights the bogus transaction of 10 SOL (or 10 billion lamports) from one to the other.
Had the team at Chorus One not identified this, we would’ve left ourselves open to a major hack if it was exploited after our Mainnet Beta launch. Therefore we want to a massive thanks to Chorus One and @Reisen | chorus.one in particular for not only successfully executing the attack, but also the amount of incredible time and effort they’ve invested in thoroughly researching our codebase in preparing for this attack.